BitLocker: How to configure BitLocker Drive Encryption on Windows 10 Clients in Microsoft Intune
The cloud-based Mobile Device Management (MDM) solution in Microsoft Intune gives mobile users the power to work productively from anywhere. At the same time, it must be ensured for the companies that the company data is protected independently of location, in particular through the consideration of the DSVO. To keep your corporate data secure, whether your administrative infrastructure is local or in the cloud, most organizations use a form of hard-disk encryption such as Microsoft BitLocker.
It was first introduced with Windows 10, version 1703 BitLocker CSP for managing BitLocker Drive Encryption over Microsoft Intune for Windows 10 MDM. The BitLocker CSP allowed administrators to request BitLocker Drive Encryption using the RequireDeviceEncryption setting. However, these settings required end user interaction to start the BitLocker Drive Encryption process. This approach from Microsoft was accepted by our customers as a non-optimal process of BitLocker Drive Encryption, so it was necessary to fully automate Bitlocker encryption through a Powershell script without prompting the end user to encrypt the drives.
Since Windows 10 version 1809 the Biltlocker CSP AllowStandardUserEncryption is available via the OMA-URI settings and currently the setting “Allow standard users to enable encryption during Azure AD Join” also exists directly over UI.
Now I’ll show you how to use the Endpoint Protection (BitLocker) policy in Intune with Windows AutoPilot. Endpoint Protection policies allow you to configure and enforce BitLocker on your Windows 10 devices. The Endpoint Protection (BitLocker) policy has been updated to include more settings, for example recently added the setting “Warning for other disk encryption”.
The prerequisites for the Intune BitLocker configuration are:
- Windows 10 Version 1809 Enterprise and Pro
- Devices connected to Azure Active Directory
- Microsoft Intune
We’ll now take a closer look at this policy and review what information we can configure in the Endpoint Protection policy in Intune:
1. Select Device Configuration and then Profiles. In the profile overview, click Create profile:
2. Enter the AutoPilot profile name, select Windows 10 and later as Platform, then End Point Protection as Profile Type. Then, under Endpoint Protection, select Windows Encryption:
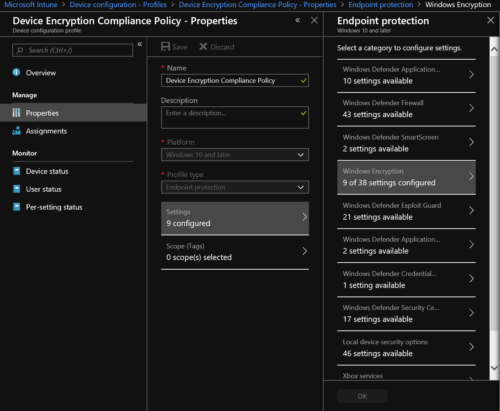
3. First, we will enforce BitLocker on Windows 10 by configuring the Windows settings in the policy.
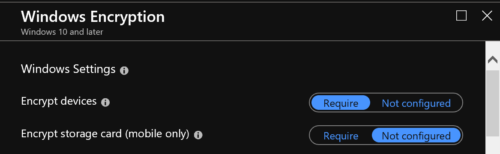
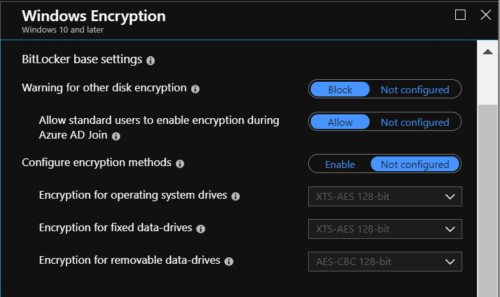
4. In the next step we configure the BitLocker base settings in the profile.
If you select Allow, BitLocker encryption will be enabled as soon as the user is logged in. You can then configure the encryption methods for the operating system drive, built-in data drives, and removable drives. If you do not configure the encryption methods, BitLocker uses the default encryption method for the drives:
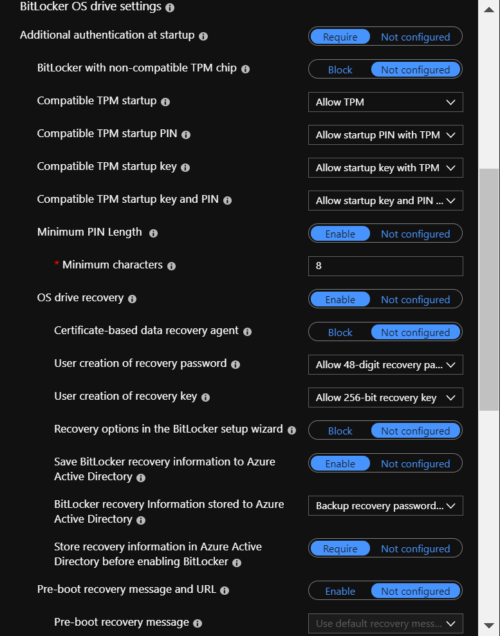
5. Here you can configure the TPM and recovery key settings. Note that I have configured to save the key in AzureAD. For administrators, the latest update to Microsoft Intune (version 1903) also provides the ability to access the BitLocker recovery key from a Windows 10-registered device in Microsoft Intune. This is the same procedure you use to access the BitLocker recovery keys through AzureAD:
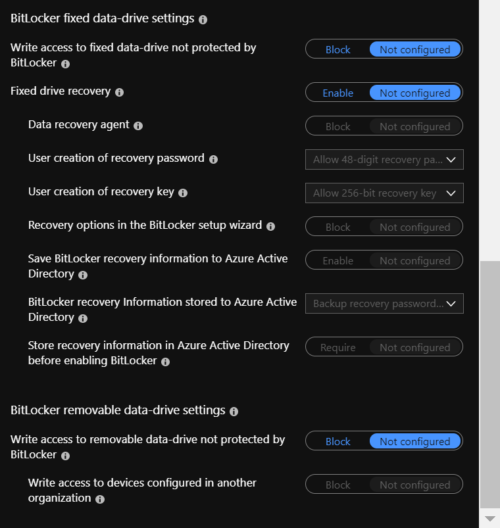
6. Here you can configure BitLocker settings for fixed and removable drives. I did not configure the policies here. The possible settings are:
7. To complete the configuration of the BitLocker settings, you must now assign the policy to the AutoPilot device group to which you want to apply the new BitLocker encryption methods.
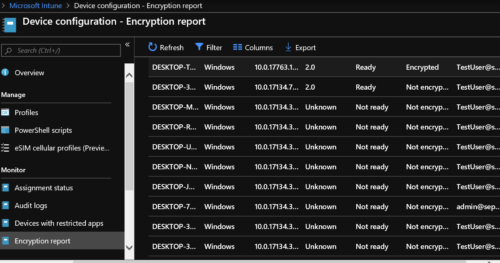
8. In Microsoft Intune you can check under “Device configuration – Encryption report”, if the BitLocker encryption of the Windows 10 Clients is successfully implemented: