New security tools new processes?
Working with the M365 Defender solution requires a change in processes. Based on our experiences from previous customer projects and Microsoft best practices, we recommend to build and establish processes for your organisation to enable yourself to fully use all M365 Defender features. The purpose of the conception and definition of the new processes is a structured “incident handling and remediation” process, as well as perspective implementation in an ITSM or documentation in a “process warehouse” for regulatory purposes. The full potential of the technical security solutions used is leveraged with this approach.
The best practise approach can be conducted through a series of workshops and remote work units to create or adapt the crucial IT Security processes due to the implementation of cloud-based Microsoft Security solution. It consists out of the element’s creation, documentation, and implementation of the following process layers:
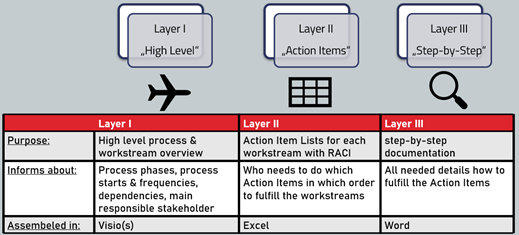
- Process layer 1 High-level (Visio Swimlane)
- Process layer 2 Action item (Excel Actions Items with RACI allocation)
- Process layer 3 Operation manual/playbook documentation (PDF as knowledge base)
- Optional: ITSM implementation & process monitoring (custom)
First, high level processes and a general workstream overview, to visualize the process phases and main responsible stakeholders. Next, each workstream from layer one is stripped down and all action-items are allocated through the RACI matrix to define responsibilities. Making sure that at each point in time everyone knows their assigned tasks. The third level consists of a step-by-step operations manual, which can be used for everyday operations by your security analysts.
The following steps are recommended:
Design Process layer 1 – high level
- high level process description
- description key use cases based on Change phases
Define process layer 2 – action item
- Definition roles, interfaces & RACI allocation
- action-item definition
Document process layer 3 – step-by-step
- step-by-step documentation (operational manual)
- onboarding documentation
- methods and tools documentation (toolkit)
Optional: Establish process monitoring
- Establishing a measurement plan (technical & UX/IT Stakeholder feedback)
- Establishing a Power BI based measurement dashboard
- Establishing and documenting the measurement process
- Appropriate actions and improvements based on the measurement results
Optional: Implementation in ITSM
- Visualizing the process
- Organizing the workflows
- Documenting the workflows
- Automizing the workflow
- Established KPI-Source for measurement/monitoring
Change Management
As new processes, especially in combination with new solutions, can bring a certain amount of resistance from your organization, we like to point out the need for extensive change and adoption management. Combining adoption and change management with joint process creation ensures that your new Microsoft Defender 365 solutions can bring the most value for you.
Challenges and risks related to this project may be the following and need to be considered and evaluated during project implementation and in periodic “weekly’s”:
- Identification of relevant process triggers & the security system landscape
- Standardization of the “incident handling and remediation process”
- Survey & Onboarding of relevant Stakeholders
- Organizational growth towards a global group
- Clear & structured preparation for “major incidents”
- Communication, importance & team resources of Security Operations activities
As the threat landscape is constantly evolving, security operations and processes have to be kept up to date. To support sustainable results, continuous improvement on monthly basis is the key to success.
sepago IT Security process consulting (sepago adapt) ensures that your security team is enabled to follow processes fitting your organization at each point in time. This makes sure that solutions like M365 Defender can unfold their full potential and fortify the safety status of your organization.
